CCNA 2 Chapter 3 v5 Exam Answers 2016
You can download fresh questions. Daily updated.
LAST UPDATE: TODAY
1
A network administrator is determining the best placement of VLAN trunk links. Which two types of point-to-point connections utilize VLAN trunking? (Choose two.)
A network administrator is determining the best placement of VLAN trunk links. Which two types of point-to-point connections utilize VLAN trunking? (Choose two.)
between two switches that share a common VLAN
between a switch and a server that has an 802.1Q NIC*
between a switch and a client PC
between a switch and a network printer
between two switches that utilize multiple VLANs*
between a switch and a server that has an 802.1Q NIC*
between a switch and a client PC
between a switch and a network printer
between two switches that utilize multiple VLANs*
2
What happens to a port that is associated with VLAN 10 when the administrator deletes VLAN 10 from the switch?
What happens to a port that is associated with VLAN 10 when the administrator deletes VLAN 10 from the switch?
The port automatically associates itself with the native VLAN.
The port creates the VLAN again.
The port goes back to the default VLAN.*
The port becomes inactive.
3
The port creates the VLAN again.
The port goes back to the default VLAN.*
The port becomes inactive.
3
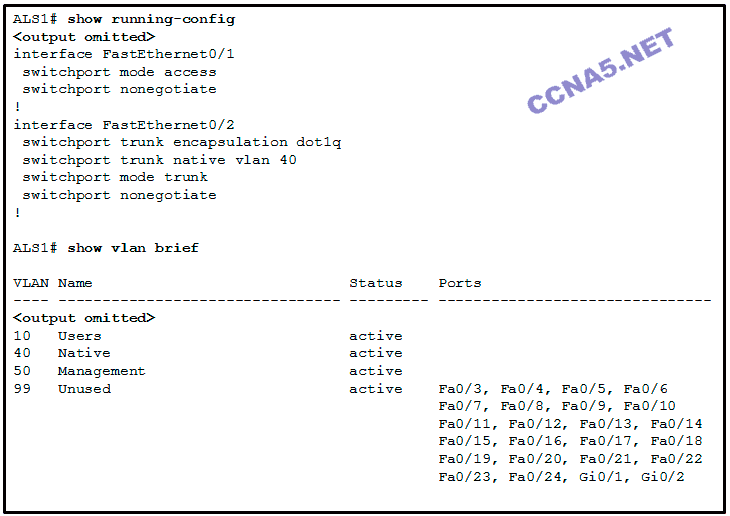
Refer to the exhibit. Interface Fa0/1 is connected to a PC. Fa0/2 is a trunk link to another switch. All other ports are unused. Which security best practice did the administrator forget to configure?
Configure all unused ports to a ‘black-hole’ VLAN that is not used for anything on the network.
Disable autonegotiation and set ports to either static access or static trunk.
Change the native VLAN to a fixed VLAN that is distinct from all user VLANs and to a VLAN number that is not VLAN 1.
All user ports are associated with VLANs distinct from VLAN 1 and distinct from the ‘black-hole’ VLAN.*
Disable autonegotiation and set ports to either static access or static trunk.
Change the native VLAN to a fixed VLAN that is distinct from all user VLANs and to a VLAN number that is not VLAN 1.
All user ports are associated with VLANs distinct from VLAN 1 and distinct from the ‘black-hole’ VLAN.*
4
Which command is used to remove only VLAN 20 from a switch?
Which command is used to remove only VLAN 20 from a switch?
no switchport access vlan 20
delete flash:vlan.dat
no vlan 20*
delete vlan.dat
delete flash:vlan.dat
no vlan 20*
delete vlan.dat
5
A Cisco Catalyst switch has been added to support the use of multiple VLANs as part of an enterprise network. The network technician finds it necessary to clear all VLAN information from the switch in order to incorporate a new network design. What should the technician do to accomplish this task?
A Cisco Catalyst switch has been added to support the use of multiple VLANs as part of an enterprise network. The network technician finds it necessary to clear all VLAN information from the switch in order to incorporate a new network design. What should the technician do to accomplish this task?
Erase the startup configuration and reboot the switch.
Erase the running configuration and reboot the switch.
Delete the startup configuration and the vlan.dat file in the flash memory of the switch and reboot the switch.*
Delete the IP address that is assigned to the management VLAN and reboot the switch.
Erase the running configuration and reboot the switch.
Delete the startup configuration and the vlan.dat file in the flash memory of the switch and reboot the switch.*
Delete the IP address that is assigned to the management VLAN and reboot the switch.
6
What is the effect of issuing a switchport access vlan 20 command on the Fa0/18 port of a switch that does not have this VLAN in the VLAN database?
What is the effect of issuing a switchport access vlan 20 command on the Fa0/18 port of a switch that does not have this VLAN in the VLAN database?
VLAN 20 will be created automatically.*
The command will have no effect on the switch.
Port Fa0/18 will be shut down.
An error stating that VLAN 20 does not exist will be displayed and VLAN 20 is not created.
7
Which command displays the encapsulation type, the voice VLAN ID, and the access mode VLAN for the Fa0/1 interface?
The command will have no effect on the switch.
Port Fa0/18 will be shut down.
An error stating that VLAN 20 does not exist will be displayed and VLAN 20 is not created.
7
Which command displays the encapsulation type, the voice VLAN ID, and the access mode VLAN for the Fa0/1 interface?
show mac address-table interface Fa0/1
show interfaces Fa0/1 switchport*
show interfaces trunk
show vlan brief
show interfaces Fa0/1 switchport*
show interfaces trunk
show vlan brief
8

Place the options in the following order:
– not scored –
dynamic auto
nonegotiate
dynamic desirable
trunk
9
Port Fa0/11 on a switch is assigned to VLAN 30. If the command no switchport access vlan 30 is entered on the Fa0/11 interface, what will happen?
9
Port Fa0/11 on a switch is assigned to VLAN 30. If the command no switchport access vlan 30 is entered on the Fa0/11 interface, what will happen?
Port Fa0/11 will be returned to VLAN 1.*
VLAN 30 will be deleted.
An error message would be displayed.
Port Fa0/11 will be shutdown.
VLAN 30 will be deleted.
An error message would be displayed.
Port Fa0/11 will be shutdown.
10
What must the network administrator do to remove Fast Ethernet port fa0/1 from VLAN 2 and assign it to VLAN 3?
What must the network administrator do to remove Fast Ethernet port fa0/1 from VLAN 2 and assign it to VLAN 3?
Enter the no vlan 2 and the vlan 3 commands in global configuration mode.
Enter the switchport trunk native vlan 3 command in interface configuration mode.
Enter the switchport access vlan 3 command in interface configuration mode.*
Enter the no shutdown in interface configuration mode to return it to the default configuration and then configure the port for VLAN 3.
Enter the switchport trunk native vlan 3 command in interface configuration mode.
Enter the switchport access vlan 3 command in interface configuration mode.*
Enter the no shutdown in interface configuration mode to return it to the default configuration and then configure the port for VLAN 3.
11
Which two Layer 2 security best practices would help prevent VLAN hopping attacks? (Choose two.)
Which two Layer 2 security best practices would help prevent VLAN hopping attacks? (Choose two.)
Disable DTP autonegotiation on end-user ports.*
Change the management VLAN to a distinct VLAN that is not accessible by regular users.
Statically configure all ports that connect to end-user host devices to be in trunk mode.
Change the native VLAN number to one that is distinct from all user VLANs and is not VLAN 1.*
Use SSH for all remote management access.
Change the management VLAN to a distinct VLAN that is not accessible by regular users.
Statically configure all ports that connect to end-user host devices to be in trunk mode.
Change the native VLAN number to one that is distinct from all user VLANs and is not VLAN 1.*
Use SSH for all remote management access.
12
In a basic VLAN hopping attack, which switch feature do attackers take advantage of?
In a basic VLAN hopping attack, which switch feature do attackers take advantage of?
automatic encapsulation negotiation
the default automatic trunking configuration*
an open Telnet connection
forwarding of broadcasts
the default automatic trunking configuration*
an open Telnet connection
forwarding of broadcasts
13
A Cisco switch currently allows traffic tagged with VLANs 10 and 20 across trunk port Fa0/5. What is the effect of issuing a switchport trunk allowed vlan 30 command on Fa0/5?
A Cisco switch currently allows traffic tagged with VLANs 10 and 20 across trunk port Fa0/5. What is the effect of issuing a switchport trunk allowed vlan 30 command on Fa0/5?
It allows only VLAN 30 on Fa0/5.*
It allows a native VLAN of 30 to be implemented on Fa0/5.
It allows VLANs 1 to 30 on Fa0/5.
It allows VLANs 10, 20, and 30 on Fa0/5.
It allows a native VLAN of 30 to be implemented on Fa0/5.
It allows VLANs 1 to 30 on Fa0/5.
It allows VLANs 10, 20, and 30 on Fa0/5.
14
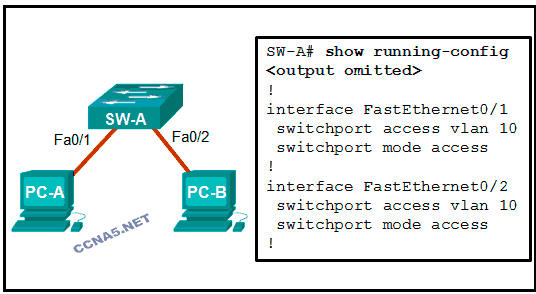
Refer to the exhibit. A frame is traveling between PC-A and PC-B through the switch. Which statement is true concerning VLAN tagging of the frame?
No VLAN tag is added to the frame.*
A VLAN tag is added when the frame is accepted by the switch.
A VLAN tag is added when the frame is forwarded out the port to PC-B.
A VLAN tag is added when the frame leaves PC-A.
A VLAN tag is added when the frame is accepted by the switch.
A VLAN tag is added when the frame is forwarded out the port to PC-B.
A VLAN tag is added when the frame leaves PC-A.
15

Refer to the exhibit. PC-A and PC-B are both in VLAN 60. PC-A is unable to communicate with PC-B. What is the problem?
The native VLAN is being pruned from the link.
The VLAN that is used by PC-A is not in the list of allowed VLANs on the trunk.*
The trunk has been configured with the switchport nonegotiate command.
The native VLAN should be VLAN 60.
The VLAN that is used by PC-A is not in the list of allowed VLANs on the trunk.*
The trunk has been configured with the switchport nonegotiate command.
The native VLAN should be VLAN 60.
16
What VLANs are allowed across a trunk when the range of allowed VLANs is set to the default value?
What VLANs are allowed across a trunk when the range of allowed VLANs is set to the default value?
All VLANs will be allowed across the trunk.*
Only the native VLAN will be allowed across the trunk.
The switches will negotiate via VTP which VLANs to allow across the trunk.
Only VLAN 1 will be allowed across the trunk.
Only the native VLAN will be allowed across the trunk.
The switches will negotiate via VTP which VLANs to allow across the trunk.
Only VLAN 1 will be allowed across the trunk.
17
Under which two occasions should an administrator disable DTP while managing a local area network? (Choose two.)
Under which two occasions should an administrator disable DTP while managing a local area network? (Choose two.)
on links that should not be trunking*
when connecting a Cisco switch to a non-Cisco switch*
on links that should dynamically attempt trunking
when a neighbor switch uses a DTP mode of dynamic auto
when a neighbor switch uses a DTP mode of dynamic desirable
18
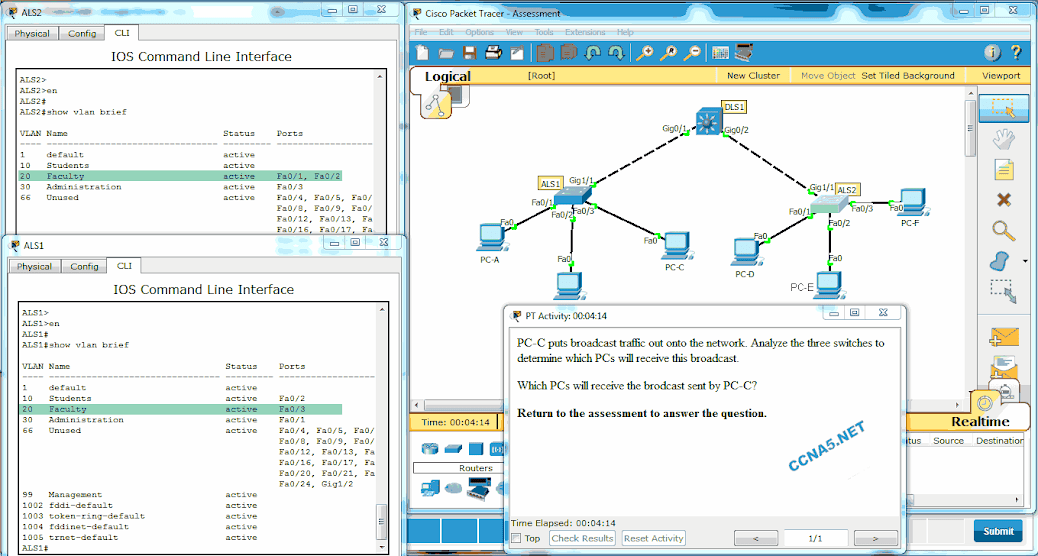
Open the PT Activity. Perform the tasks in the activity instructions and then answer the question.
Which PCs will receive the broadcast sent by PC-C?
when connecting a Cisco switch to a non-Cisco switch*
on links that should dynamically attempt trunking
when a neighbor switch uses a DTP mode of dynamic auto
when a neighbor switch uses a DTP mode of dynamic desirable
18

Open the PT Activity. Perform the tasks in the activity instructions and then answer the question.
Which PCs will receive the broadcast sent by PC-C?
PC-D, PC-E*
PC-A, PC-B, PC-D, PC-E
PC-A, PC-B
PC-A, PC-B, PC-D, PC-E, PC-F
PC-A, PC-B, PC-E
PC-A, PC-B, PC-D, PC-E
PC-A, PC-B
PC-A, PC-B, PC-D, PC-E, PC-F
PC-A, PC-B, PC-E
19
Which two statements are true about VLAN implementation? (Choose two.)
Which two statements are true about VLAN implementation? (Choose two.)
The network load increases significantly because of added trunking information.
Devices in one VLAN do not hear the broadcasts from devices in another VLAN.*
The size of the collision domain is reduced.
VLANs logically group hosts, regardless of physical location.*
The number of required switches in a network decreases.
Devices in one VLAN do not hear the broadcasts from devices in another VLAN.*
The size of the collision domain is reduced.
VLANs logically group hosts, regardless of physical location.*
The number of required switches in a network decreases.
20

Refer to the exhibit. DLS1 is connected to another switch, DLS2, via a trunk link. A host that is connected to DLS1 is not able to communicate to a host that is connected to DLS2, even though they are both in VLAN 99. Which command should be added to Fa0/1 on DLS1 to correct the problem?
switchport trunk allowed vlan add 99
switchport trunk native vlan 66*
switchport mode dynamic auto
switchport nonegotiate
switchport trunk native vlan 66*
switchport mode dynamic auto
switchport nonegotiate
21
Which switch feature ensures that no unicast, multicast, or broadcast traffic is passed between ports that are configured with this feature?
Which switch feature ensures that no unicast, multicast, or broadcast traffic is passed between ports that are configured with this feature?
switch port security
PVLAN protected port*
ACL
VLAN
PVLAN protected port*
ACL
VLAN
22
Fill in the blank. Use the full command syntax.
The ” show vlan brief ” command displays the VLAN assignment for all ports as well as the existing VLANs on the switch.
Fill in the blank. Use the full command syntax.
The ” show vlan brief ” command displays the VLAN assignment for all ports as well as the existing VLANs on the switch.
23
Which three statements accurately describe VLAN types? (Choose three).
Which three statements accurately describe VLAN types? (Choose three).
An 802.1Q trunk port, with a native VLAN assigned, supports both tagged and untagged traffic.*
A management VLAN is any VLAN that is configured to access management features of the switch.*
A data VLAN is used to carry VLAN management data and user-generated traffic.
Voice VLANs are used to support user phone and e-mail traffic on a network.
VLAN 1 is always used as the management VLAN.
After the initial boot of an unconfigured switch, all ports are members of the default VLAN.*
24
Which command should the network administrator implement to prevent the transfer of DTP frames between a Cisco switch and a non-Cisco switch?
A management VLAN is any VLAN that is configured to access management features of the switch.*
A data VLAN is used to carry VLAN management data and user-generated traffic.
Voice VLANs are used to support user phone and e-mail traffic on a network.
VLAN 1 is always used as the management VLAN.
After the initial boot of an unconfigured switch, all ports are members of the default VLAN.*
24
Which command should the network administrator implement to prevent the transfer of DTP frames between a Cisco switch and a non-Cisco switch?
S1(config-if)# switchport mode trunk
S1(config-if)# switchport mode access
S1(config-if)# switchport nonegotiate*
S1(config-if)# switchport mode dynamic desirable
S1(config-if)# switchport trunk allowed vlan none
S1(config-if)# switchport mode access
S1(config-if)# switchport nonegotiate*
S1(config-if)# switchport mode dynamic desirable
S1(config-if)# switchport trunk allowed vlan none
NEW QUESTION
25 Which combination of DTP modes set on adjacent Cisco switches will cause the link to become an access link instead of a trunk link?
dynamic auto – dynamic auto*
dynamic desirable – dynamic desirable
dynamic desirable – trunk
dynamic desirable – dynamic auto
dynamic desirable – dynamic desirable
dynamic desirable – trunk
dynamic desirable – dynamic auto
26. An administrator has determined that the traffic from a switch that corresponds to a VLAN is not being received on another switch over a trunk link. What could be the problem?
trunk mode mismatch
allowed VLANS on trunks*
native VLANS mismatch
dynamic desirable mode on one of the trunk links
allowed VLANS on trunks*
native VLANS mismatch
dynamic desirable mode on one of the trunk links
27. What is the default DTP mode on Cisco 2960 and 3560 switches?
trunk
dynamic auto*
access
dynamic desirable
dynamic auto*
access
dynamic desirable
28. Refer to the exhibit. What can be determined from the output that is shown?
Interface FastEthernet 0/1 is configured with the switchport protected command.*
Interface FastEthernet 0/1 is configured with the nonegotiate keyword.
Interface FastEthernet 0/1 is trunking and using Native VLAN 1.
Interface FastEthernet 0/1 is configured as dynamic auto by the administrator.
Interface FastEthernet 0/1 is configured with the nonegotiate keyword.
Interface FastEthernet 0/1 is trunking and using Native VLAN 1.
Interface FastEthernet 0/1 is configured as dynamic auto by the administrator.
29. Which two characteristics match extended range VLANs? (Choose two.)
They are saved in the running-config file by default.*
CDP can be used to learn and store these VLANs.
VLAN IDs exist between 1006 to 4094.*
They are commonly used in small networks.
VLANs are initialized from flash memory.
CDP can be used to learn and store these VLANs.
VLAN IDs exist between 1006 to 4094.*
They are commonly used in small networks.
VLANs are initialized from flash memory.
30. Match the IEEE 802.1Q standard VLAN tag field in the description. (not all options are used)
Place the options in the following order:
User Priority – value that supports level or service implementation
Type – value for the tag protocol ID value
Canonical Format Identifier – identifier that enables Token Ring frames to be carried across Ethernet Links
– not scored – -value for the application protocol of the user data in a frame
VLAN ID – VLAN number
User Priority – value that supports level or service implementation
Type – value for the tag protocol ID value
Canonical Format Identifier – identifier that enables Token Ring frames to be carried across Ethernet Links
– not scored – -value for the application protocol of the user data in a frame
VLAN ID – VLAN number
31. Which type of VLAN is used to designate which traffic is untagged when crossing a trunk port?
data
default
management
native*
32. What are three primary benefits of using VLANs? (Choose three.)
security*
a reduction in the number of trunk links
improved IT staff efficiency*
cost reduction*
no required configuration
end user satisfaction
33. What happens to switch ports after the VLAN to which they are assigned is deleted?
The ports are disabled.
The ports are assigned to VLAN1, the default VLAN.
The ports stop communicating with the attached devices.*
The ports are placed in trunk mode.
34. Which two modes does Cisco recommend when configuring a particular switch port? (Choose two.)
trunk*
IEEE 802.1Q
access*
Gigabit Ethernet
FastEthernet
ISL

No comments:
Post a Comment